

DDoS Shield
Automated cyberthreat detection and mitigation technology that works in real time to scan for malicious traffic and block it, before it affects your network.
Protect your organization from cybersecurity threats with industry-leading security solutions.
Optimize your day-to-day with solutions tailored to the needs of your organization.
Avoid disruption with data backup and network alternatives.
Maximize the value of your IT spend with cost-efficient technology and solutions that scale.
Design the ideal IT infrastructure for your remote or hybrid workplace.
Grow your business with flexible IT designed to grow with it.
Learn more about our products and how they can benefit your business.
Discover ICT trends, strategies, and news stories.
Find out about Acronym's mission and approach to serving our customers.
Discover expert advice and discussions on the latest trends.
Browse through frequently asked questions to learn more.
Discover expert advice and discussions on the latest trends.
Read into what makes Acronym the only telecom of its kind in Canada.
Stay up to date on what's happening and what's ahead at Acronym.
Explore career opportunities at the frontline of cutting edge communications technology.

Distributed Denial of Service (DDoS) attacks aim to cripple an organization’s network, servers and applications by overwhelming them with malicious traffic. Such attacks can severely limit your ability to function and lead to tens of thousands of dollars in lost revenue, mitigation costs and consumer trust. And the threat is growing. According Cisco Annual Internet Report, it is estimated that the total number of DDoS attacks will double to 15.4 million in 2023, from 7.9 million in 2018.
Many enterprises and organizations use firewalls to protect against DDoS attacks. Although firewalls can protect networks from a variety of security issues, they are not designed to detect and mitigate large-scale DDoS attacks. There are three main reasons for this.
Firewalls are designed to keep suspicious network traffic from breaching the perimeter of an organization’s systems. The firewall filters incoming packets of information, checking to see if they meet specific criteria before allowing them through. However, when confronted with excessive traffic, the firewall may slow the transmission process, leading to disruptions of data flows and network downtime.
“WHEN CONFRONTED WITH EXCESSIVE TRAFFIC, THE FIREWALL MAY SLOW THE TRANSMISSION PROCESS, LEADING TO DISRUPTIONS OF DATA FLOWS AND NETWORK DOWNTIME.”
In addition, firewalls are “stateful” – that is, they have to keep track of the full state of active network traffic to deliver protection. The memory and processing resources required to store and filter this information can make them a soft target for DDoS attackers, who can easily overwhelm them with volumetric attacks, take your network offline and block legitimate users from establishing connections.
Firewalls aim to prevent the intrusion of one packet of information at a time – it’s how they filter incoming information and ensure it is legitimate. But firewalls are not designed to detect the combined actions of legitimate packets of data sent millions of times. DDoS attacks such as HTTP floods are designed to overwhelm a server with millions of seemingly legitimate HTTP requests. Each individual session appears legitimate and is not marked as a threat by firewalls. But firewalls are not designed to look at the behaviour of millions of concurrent sessions as a whole, which limits their ability to recognize an attack. When the targeted server becomes saturated with HTTP requests and is unable to respond to normal traffic, denial of service can occur for legitimate users.
Some DDoS attacks are also staged by creating thousands of fake source IP addresses, making it difficult to identify the location of the attacking machines. These fake addresses can sometimes trick the firewall into thinking they are legitimate, allowing the attack to slip through.
To effectively protect themselves against DDoS attacks, organizations need a defence strategy that will stop an attack before it reaches their network firewalls. Most intrusion detection solutions are deployed too close to the protected servers – and not as the first line of defence. However, when faced with volumetric attacks, this is too far down the road to offer much protection.
“A DDOS SOLUTION THAT COMPLEMENTS A FIREWALL, AND WHICH ALLOWS LEGITIMATE TRAFFIC TO FLOW THROUGH, IS THE MOST EFFECTIVE APPROACH TO ADDRESS VOLUMETRIC DDOS ATTACKS.”
A dedicated DDoS mitigation strategy is best deployed before traffic reaches your hand-off from the Internet Service Provider – providing true early detection and mitigation of a potential attack before it reaches your firewall. A DDoS solution that complements a firewall, and which allows legitimate traffic to flow through, is the most effective approach to address volumetric DDoS attacks.
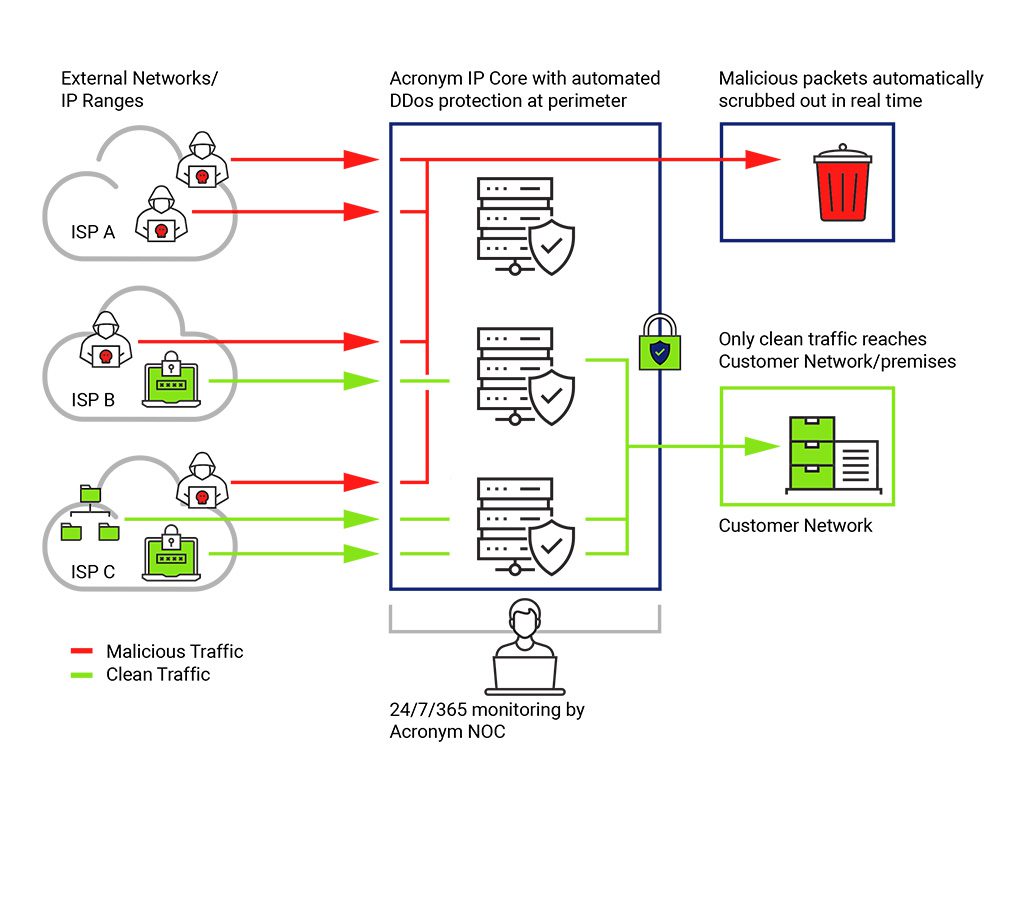

DDoS Shield from Acronym can protect your business from the dangers of DDoS attacks before they reach your network. DDoS Shield makes use of automated cyber threat detection and mitigation technology that works in real time to monitor for malicious traffic and block it before it can affect your network. Because the detection and mitigation of your traffic is contained within Acronym’s network in Canada, network latency is kept to a minimum and your data remains under Canadian jurisdiction.
Featuring 24/7/365 detection and mitigation in seconds, plus an easy-to-use portal for comprehensive visibility into your threat landscape, DDoS Shield can provide your business with protection and peace of mind.


Automated cyberthreat detection and mitigation technology that works in real time to scan for malicious traffic and block it, before it affects your network.
Acronym Solutions Inc. is a full-service information and communications technology (ICT) company that provides a range of scalable and secure Network, Voice & Collaboration, Security, Cloud and Managed IT Solutions. We support Canadian businesses, large enterprises, service providers, healthcare providers, public-sector organizations and utilities. We leverage our extensive network expertise to design and build customized, fully scalable solutions to help our customers grow their businesses and realize their full potential. With more than 20 years’ experience managing the communications system that enables Ontario’s electrical grid, Acronym is uniquely positioned to understand the mission-critical needs of any business to deliver the innovative and reliable services that respond to the changing demands of businesses, and support rapid growth and digital transformation initiatives.