

Autonomous AI powered endpoint security solution backed by world-class managed security services
Secure IT – Endpoint Detection and Response (EDR) delivers differentiated endpoint protection by preventing, detecting and acting on ever-changing threats, allowing for a quick recovery when exploitations, such as ransomware, occur. We offer resource-efficient autonomous agents for Windows, Mac, Linux, and Kubernetes and support various form factors, including physical, virtual, VDI, customer data centers, hybrid data centers, and cloud service providers. Secure IT – Endpoint Detection and Response is powered by SentinelOne.
How it works

FULL ENDPOINT PROTECTION
Powered by SentinelOne, the cloud managed solution includes comprehensive, autonomous features to protect your environment against all threats.
MONTHLY SUBSCRIPTION
Pay one flat monthly fee per device, to simplify your billing.
CENTRALLY MANAGED 24/7/365
Network and security specialists continuously monitor your endpoints for incidents and threat actors, only escalating to your team when required.
DATA-DRIVEN DASHBOARDS AND ANALYTICS
Get access to view your endpoint health and security posture in real time.
Integration
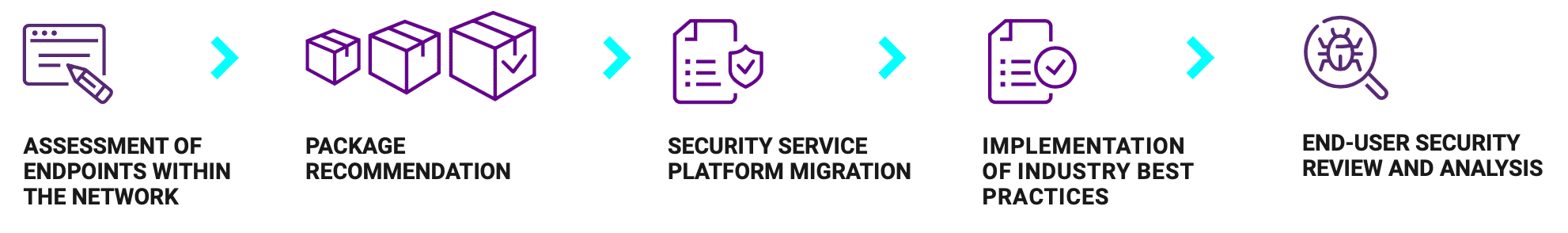
Secure IT – Endpoint Detection and Response (EDR) is designed to rapidly deploy protection to your endpoints. We use industry best practices with customized security policies and processes that respond to evolving threat actors that target endpoints. Our deployment team works hand in hand with your staff to assess, design and deploy the solution to deliver advanced security services from day one with minimal impact to users. In addition to delivering timely support solutions with a more intimate understanding of your environment, our service offers expertise for day-to-day management of security operations and tailored program guidance — all with your success in mind.
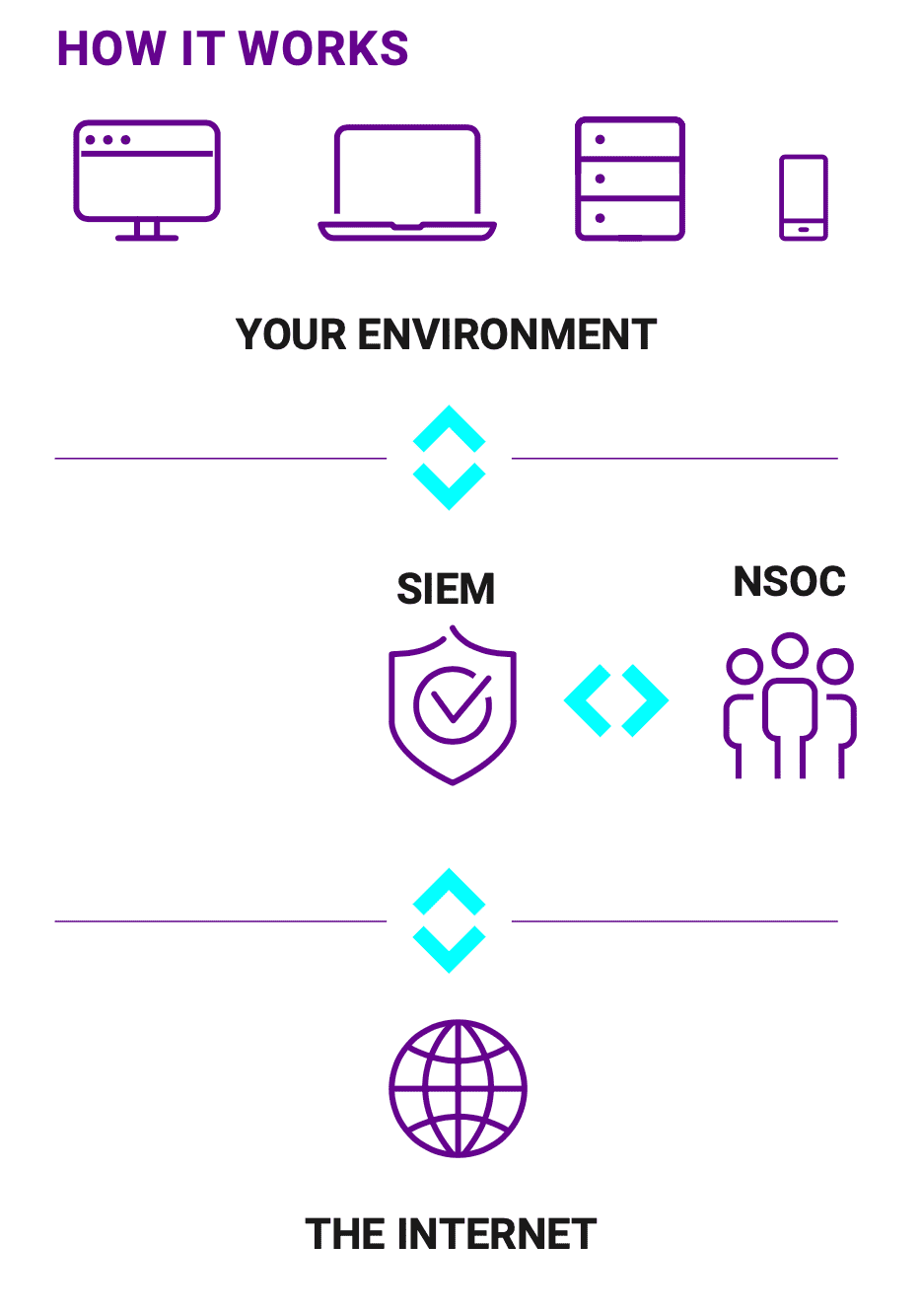
Our team and platform
SECURITY INFORMATION & EVENT MANAGEMENT
Our SIEM system uses sophisticated machine learning to determine if a threat is taking place by analyzing security events within your environment for remediation.
NETWORK AND SECURITY OPERATIONS CENTRE
We count on a team of security specialists, processes, and technology to continuously monitor customer environments in near real-time.
LEADING EDGE SOFTWARE
Includes antivirus, exploit prevention, ransomware protection, malware protection, desktop firewall, sandboxing, and endpoint containment.

BUNDLED FEATURES
| ESSENTIALS | ESSENTIALS PLUS | |
| BASE ENDPOINT FEATURES | ||
| 24/7/365 Monitoring, Policy Management, Incident Management, SIEM Integration | ||
| Artificial Intelligence Based Real-Time Endpoint Detection and Response | ||
| Autonomous Threat Response (Windows, Mac, Linux) | ||
| Autonomous Rollback Response (Windows) | ||
| Remote Network Quarantine for Endpoint | ||
| Agent Anti-Tamper on Endpoint | ||
| IT OPS / SECURITY SUITE FEATURES | ||
| OS Firewall Control with Location Awareness (Windows, Mac, Linux) | ||
| USB Device Control (Windows, Mac) | ||
| Bluetooth / Bluetooth Low Energy Control (Windows, Mac) |
About Acronym
Acronym Solutions Inc. is a full-service information and communications technology (ICT) company that provides a range of scalable and secure Network, Voice & Collaboration, Security, Cloud and Managed IT Solutions. We support Canadian businesses, large enterprises, service providers, healthcare providers, public-sector organizations and utilities. We leverage our extensive network expertise to design and build customized, fully scalable solutions to help our customers grow their businesses and realize their full potential. With more than 20 years’ experience managing the communications system that enables Ontario’s electrical grid, Acronym is uniquely positioned to understand the mission-critical needs of any business to deliver the innovative and reliable services that respond to the changing demands of businesses, and support rapid growth and digital transformation initiatives.